Cloud Workflow Automation (CWA)
Your Cloud. De-risked
Build and play automated remediation workflows with a no-code orchestration platform (Qualys Flow) with enterprise-grade precision.
De-risk your cloud with Qualys Flow, a CWA Platform - an integral part of Qualys TotalCloud™
Simplify workflow creation
Build no-code workflows with intuitive drag-and-drop nodes, allowing anyone to automate processes and tackle custom use cases without any programming expertise.
Speed up workflow creation and implementation, as no-code platforms eliminate the need for lengthy coding, testing, and deployment cycles-enabling rapid response to changing business needs.

Easily customize security control
Align with your organization's custom requirements without professional services, enabling swift adaptation to changing business needs and enhanced operational efficiency.
Implement automated security workflows across complex environments to streamline remediation processes, reduce alert overload, and ensure critical security issues are routed to the right teams at the right time.

Enrich security teams
Free up security teams from mundane tasks, allowing them to focus on high-priority security issues.
Simplify security program management through automation, improving efficiency and reducing manual errors.
Gain better visibility and control over security operations, enabling more effective monitoring and response to security threats.

Orchestrate end-to-end remediation workflows
Comprehensive remediation workflows that cover the entire incident response lifecycle.
Integrate with DevOps and ITSM tools to ensure smooth workflows and minimize manual handoffs.
Enforce consistent, policy-driven responses across teams, reducing errors and accelerating incident resolution.

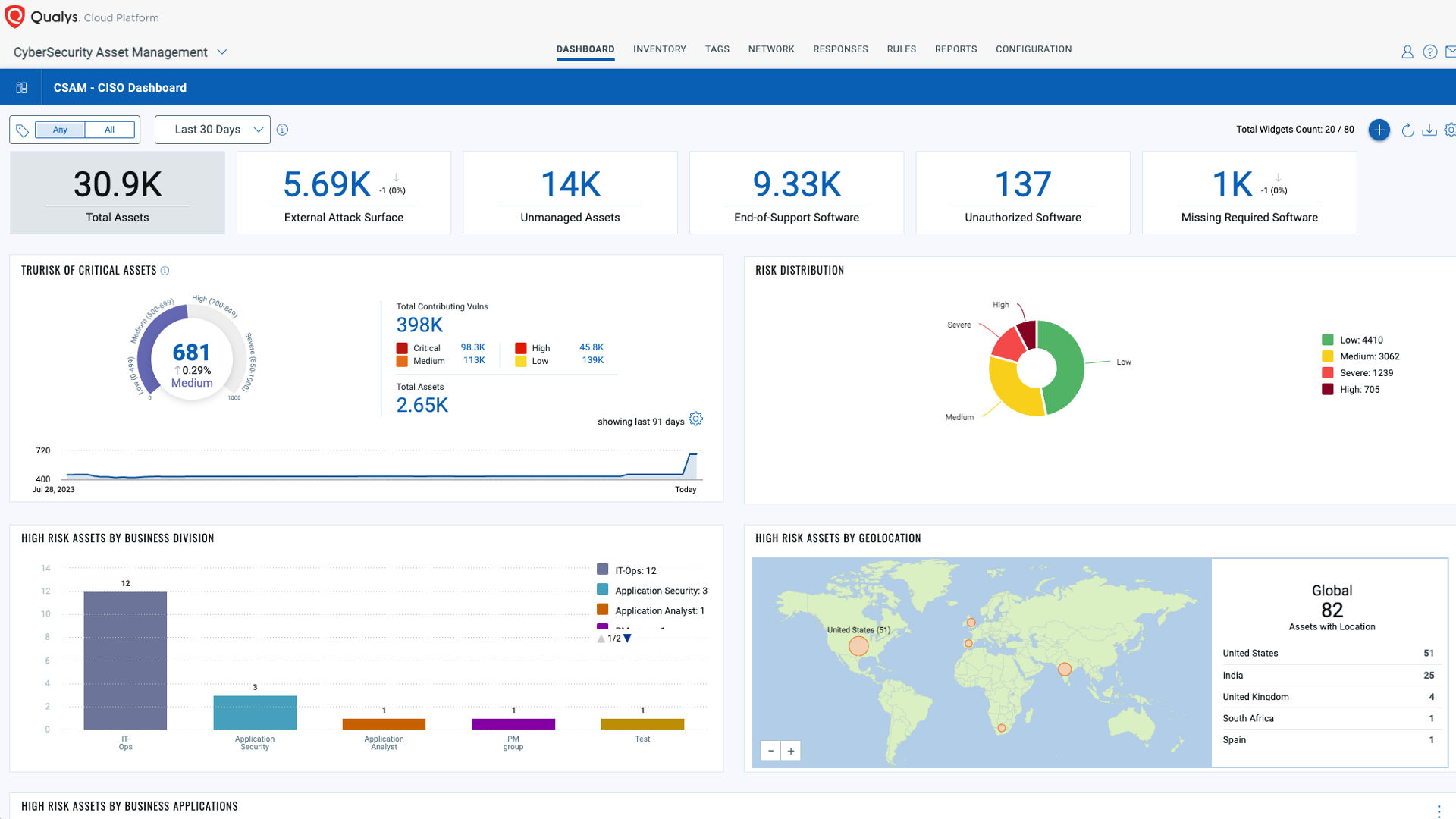
Powered by the Enterprise TruRiskTM Platform
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.







